Detection – Response + Action
Our team offers services to proactively monitor, detect, and respond to the toughest cyber threats, providing expertise without having to hire and manage yourself. We offer you the services and operations of a private security contract in the cyber and internet space. Decisive counteraction and robust response will deter any future criminal actors and attackers.
Capabilities include:
- Cyber incident hunting, detection, and response
- Managed and hybrid operate security services
- Advising and implementing solutions
- Cyber threat intelligence and analytics
- Security operations development

Integrated + Complete Cyber Security Solutions for Businesses and the Defence Industry
We design and implement transformational enterprise security programs, organizational constructs, and capabilities, so you can better manage cyber risks aligned with business priorities.
Capabilities include:
- Cyber assessments, frameworks, and benchmarking
- Cyber strategy and program transformation
- Cyber metrics, reporting, and risk quantification
- Cyber awareness, board reporting, and training
- Integrated risk management/governance, risk management, and compliance
- Third-party cyber risk
- Insider threat programs

Data and Privacy
We’ll assist you with data discovery, collection, processing, sharing, protection, archiving, and deletion. Deloitte enables data privacy and protection across the data life cycle, building sustainable, scalable programs designed around strategic principles that address operational and regulatory requirements holistically.
Capabilities include:
- Strategy
- Reporting and validation
- Architecture
- Privacy
- Protection

Application Security
We integrate cybersecurity and compliance activities throughout the software development life cycle with services to advise, design, build, deploy, and operate secure applications.
Capabilities include:
- Concept and requirements
- Design and development
- Verification and authentication
- Production
- Maintenance and retirement
- DevSecOps

Infrastructure Security
As technology continues to revolutionize business, and threats to operations become increasingly complex, organizations need to transform how they secure their enterprise. We provide services to assess, strategize, architect, implement, and operate next-generation technologies, helping to limit your risks and exposure.
Capabilities include:
- Core infrastructure security
- Cloud infrastructure security
- Attack surface management
- Zero trust
- Technology asset management
- Mobile and endpoint security
- Technical resilience

Identity Protection
We provide methodologies, along with services for implementation and operation of identity platforms to help your organization manage which employees, partners, suppliers, customers, consumers, and citizens can access sensitive organizational applications and data.
Capabilities include:
- Identity strategy
- Identity governance and administration
- Access and advanced authentication
- Privileged access management
- Consumer, customer, and citizen identity and access management
- Directory services
- Cloud and hosted identity solutions
- Identity analytics
- Emerging identity services (biometric, behavioural analytics, blockchain, AI, RPA, others)
- Identity operations and managed services
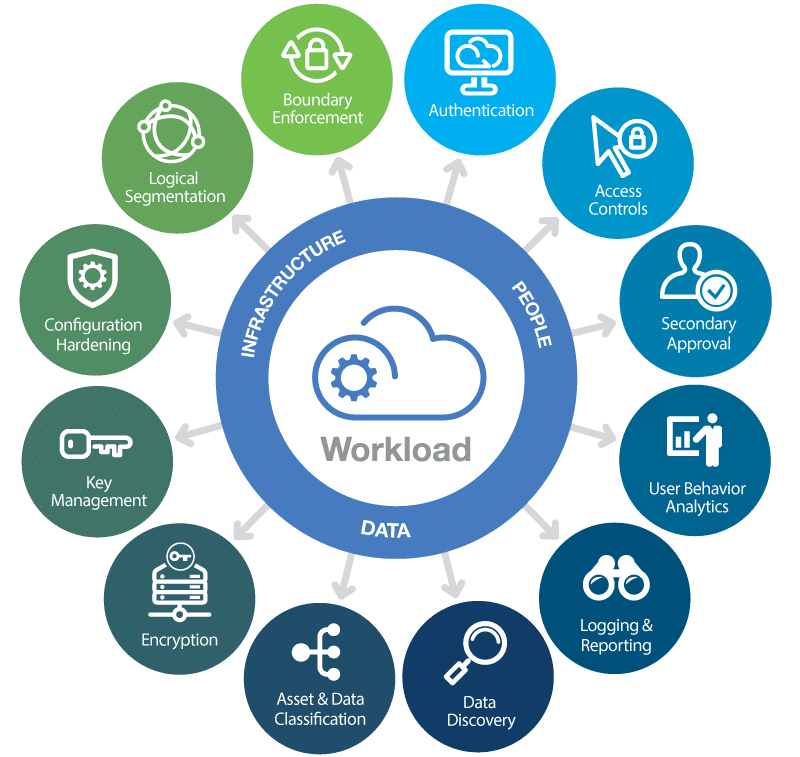
Cloud Security + Protection
We offer a distinct vision for securing your cloud environments through the lenses of business risk, regulatory, technology, and cyber, providing implementation and operation services for a broad set of cloud transformation solutions.
Capabilities include:
- Application modernization and migration
- Cloud security policy orchestration and automation
- Cyber cloud managed services
- Secure landing zones
- DevSecOps
- Cloud security analytics

Cutting Edge + Emerging Technologies
Leverage our cutting-edge capabilities to navigate the potential risk and opportunities unfolding in the ever-evolving cyber and strategic risk landscape, with services to implement and operate certain solutions.
Capabilities include:
- Internet of Things
- Secure supply chain
- 5G, advanced connectivity, and edge cyber
- Quantum
- Blockchain and digital assets
- Metaverse